What is an Intrusion Detection System (IDS)?
The question isn’t if a cyber attack will happen anymore, but when it will happen. As threats become more frequent and more sophisticated, you need a vigilant watchdog guarding your networks. That watchdog is an Intrusion Detection System (IDS).
You can think of an IDS as an alarm system for your digital assets. It operates in the background and constantly monitors network traffic and system activity for any sign of a breach or malicious behaviour. When it spots a potential threat, it instantly alerts you, giving your security team the critical time needed to react before significant damage occurs.
This blog post will break down everything you need to know about Intrusion Detection Systems. I’ll explain how they work, the different types available, how they satisfy compliance requirements, and how to choose the right solution to protect your business.
What Exactly is an Intrusion Detection System?
An intrusion detection system (IDS) is a foundational cybersecurity technology that monitors network traffic and system activity for signs of malicious behaviour or network policy violations. It functions as a critical surveillance tool, providing visibility into the health of your digital environment.
The core purpose of an IDS is not necessarily to prevent an attack, but to detect and alert you when something is going on. It identifies potential threats as they happen and immediately notifies security administrators. This early warning gives your technical teams the time required to investigate the issue and respond before a minor incident escalates into a major data breach.

How Does an Intrusion Detection System Work?
The operation of an IDS can be broken into a continuous cycle: data collection, analysis, and alerting. First, the system gathers information from different points within your network or from a specific host computer. This data is then passed to an analysis engine that scrutinizes it for threatening patterns. This analysis is the most important step and is accomplished through 2 distinct methods: signature-based detection and anomaly-based detection. If the analysis flags something as suspicious, the system generates an alert, which is logged and sent to a management console for review.
The 4 Main Types of Intrusion Detection Systems
Intrusion detection systems are specialized tools designed to monitor different parts of your IT infrastructure. Understanding the primary types is key to deploying them effectively. The main distinction between them is their scope a.k.a. whether they watch the entire network or focus on a single device.
Network Intrusion Detection System (NIDS)
An NIDS is strategically placed at points within a network, like at a firewall or the main internet gateway, to monitor all data traffic flowing to and from connected devices. An NIDS can detect malicious activity, unauthorized access attempts, and port scanning across an entire segment of the network.
The biggest benefit to this type is its broad visibility. A single NIDS can protect many devices at once without requiring any software to be installed on each of the individual machines. However, its effectiveness can be limited by encryption which means if traffic is encrypted, an NIDS cannot inspect its contents unless it is configured to decrypt it.
Host Intrusion Detection System (HIDS)
A Host Intrusion Detection System (HIDS) runs as a software agent on a single computer or server (the “host”). Unlike an NIDS that watches traffic between devices, an HIDS monitors the internal activities of the machine it’s installed on. It examines system logs, monitors critical system files for unauthorized changes, and tracks running processes.
The strength of an HIDS is its detailed insight. It can detect malicious activity that an NIDS might miss, such as malware that has been executed on the host or unauthorized changes made by a legitimate user. Because it operates within the host, it can also analyze traffic after it has been decrypted. The main challenge with it is deployment and management, as an HIDS agent must be installed and maintained on every device you wish to protect.
Protocol-Based Intrusion Detection System (PIDS)
A Protocol-Based Intrusion Detection System (PIDS) is a more specialized tool that focuses on monitoring a specific communication protocol. Typically, it is installed on a server to monitor and interpret the server’s communication with its clients.
For example, a PIDS might be deployed on a web server to exclusively monitor the conversation between that server and users’ browsers via the Hypertext Transfer Protocol (HTTP). By focusing solely on this protocol, it can provide a highly detailed and efficient analysis of potential web-based attacks.

Application Protocol-Based Intrusion Detection System (APIDS)
An Application Protocol-Based Intrusion Detection System (APIDS) is a further specialization of a PIDS. This system focuses on monitoring how an application uses its designated protocols. While a PIDS analyzes the general rules of the protocol, an APIDS analyzes the specific commands or content being sent within that protocol.
For instance, an APIDS on a database server would not just monitor the general network connection; it would analyze the specific SQL commands being sent to the database. This allows it to detect sophisticated attacks like SQL injection, where an attacker embeds malicious commands within what otherwise appears to be a legitimate request.
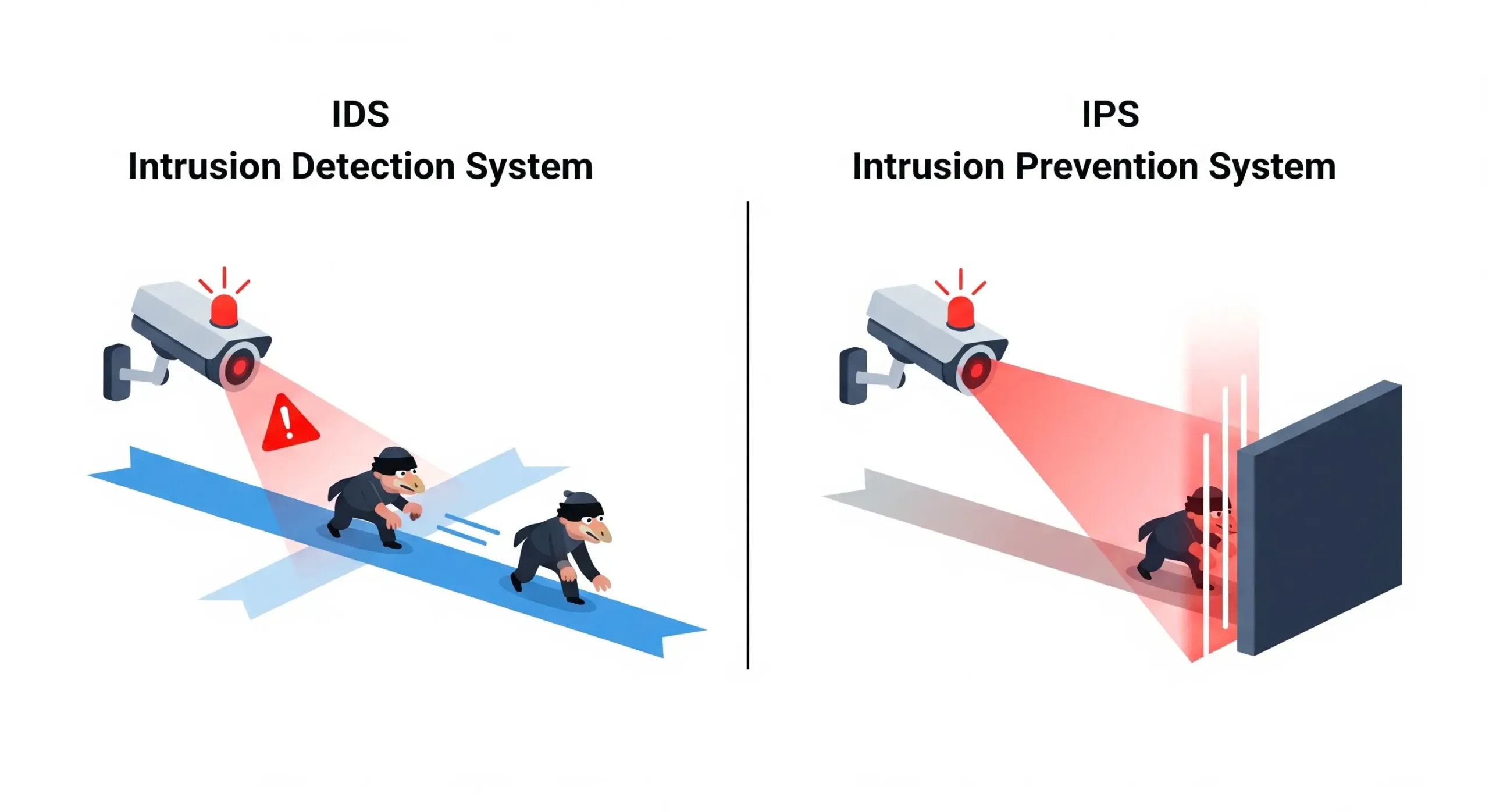
IDS vs. IPS: What’s The Difference?
IDS and IPS are often used together, leading to frequent confusion between the two. While both are designed to identify threats, they perform fundamentally different actions once a threat is found. Understanding this distinction is essential for building a robust security strategy.
An Intrusion Detection System (IDS) is a passive monitoring tool. As we’ve discussed, its job is to detect suspicious activity, log the details, and send an alert to security administrators. It acts more like a smoke detector that warns you when there is a fire, but doesn’t take any action to put the fire out. The IDS sits “out-of-band,” meaning it analyzes a copy of the network traffic, so it does not interfere with the actual flow of data.
An Intrusion Prevention System (IPS), by contrast, is an active control system. It combines the detection capabilities of an IDS with automated prevention features. An IPS sits “in-line,” directly in the path of network traffic. When it detects malicious activity, it can take immediate action to block it. This could involve dropping malicious packets, blocking traffic from the offending IP address, or resetting the connection. Following the fire analogy, an IPS is like a fire sprinkler system: it detects the fire and automatically acts to extinguish it.
Ultimately, IDS and IPS are complementary to each other. An IDS provides invaluable insight and logging for security analysis and incident response, while an IPS provides a critical layer or automated, active defense. Many modern security solutions have evolved into Intrusion Detection and Prevention Systems (IDPS), which combine the functions of both into a single platform.
Examples of IDS in Action
To understand the real-world value of an intrusion detection system, it helps to see how different industries rely on it. While the technology is all essentially the same, its application can be tailored to solve specific security challenges.
1. The Financial Sector: Protecting Transactions
Banks and financial institutions are huge targets for cyber attacks. They typically use IDS to monitor traffic flowing to and from their core banking systems and customer databases. An IDS might detect an unusual number of failed login attempts against a set of customer accounts from an unknown IP address. It would immediately flag this as a potential brute-force attack, allowing security teams to block the source before accounts are compromised and to ensure the integrity of financial data.
2. Healthcare: Safeguarding Patient Data
For healthcare organizations, protecting electronic protected health information is a top priority, mandated by regulations like HIPAA. Host-based Intrusion Detection Systems are often deployed on servers that store patient records. An HIDS agent on a hospital’s database server could detect when a user’s credentials are used to access hundreds of patient records outside of normal working hours. This anomalous behaviour would trigger an alert for immediate investigation, helping to prevent a massive data breach.
3. E-Commerce: Securing Online Stores
E-commerce platforms handle a high volume of traffic and sensitive payment information, making them vulnerable to web-based attacks. They use a combination of network and application-level IDS to secure their infrastructure. An Application Protocol-IDS monitoring a retail website could analyze the data being submitted in a “search” field. If it detects malicious SQL commands hidden within the search query (a classic SQL injection attack) it would alert admins that an attacker is attempting to bypass security to steal customer credit card information from the database.

Best Practices For Successful IDS Implementation
Deploying an IDS is more than just downloading a piece of software or installing some hardware; it requires a strategic approach to be truly effective. An improperly configured IDS can create a flood of false alerts or, worse, miss genuine threats. Following these best practices will ensure your IDS serves as a valuable asset rather than a noisy distraction.
1. Define Clear Security Objectives
Before you deploy anything, you need to know what it is you are trying to protect. Identify your most critical assets, such as sensitive customer databases, intellectual property, or financial systems. Knowing your priorities will help you decide what types of IDS to use, where to place it, and how to configure its rules to focus on your biggest risks.
2. Place Sensors Strategically
The effectiveness of an IDS is highly dependent on its location.
- For NIDS: Place sensors at critical network choke points, such as behind your main firewall, at the gateway to the internet, or in front of server farms. This ensures you have visibility into the most important traffic flows.
- For HIDS: Install agents on your most valuable servers and endpoints, including web servers, database servers, and domain controllers. This provides deep insight into the activity on your most essential machines.
3. Establish a Clean Baseline and Tune Continuously
Allow the IDS to run for a period to learn what “normal” activity looks like on your network before turning on alerts. Once active, the single most important ongoing task is tuning. You must regularly review alerts, distinguish true threats from false positives, and adjust the rules accordingly. This process reduces alert fatigue and ensures your security team can focus on real incidents.
4. Integrate With Your Security Ecosystem
To maximize its value, integrate with other security tools. Forwarding IDS alerts to a Security Information and Event Management (SIEM) system allows you to correlate threat data with logs from other sources, like firewalls and servers, giving you a much richer context for investigations.

5. Develop a Formal Incident Response Plan
An alert is useless if no one knows what to do with it. You must create a clear, documented plan that outlines the exact steps to take when a high-priority IDS alert is triggered. This should include who is responsible for investigating, how to assess the threat’s severity, and the procedure for containment and recovery.
6. Keep the System and Its Signatures Updated
The cybersecurity landscape changes daily. Keep your IDS software and its threat signature database updated regularly. New attack methods are constantly being developed and an IDS with outdated signatures is like a security guard using a 2 year-old wanted list: it’s guaranteed to be missing the latest threats.
Final Thoughts
While understanding the principles of an IDS is the first step, choosing, implementing, and tuning the right solution can be a complex challenge. This is where we can help at Lighthouse Integrations. Our team of security experts specializes in designing and deploying IDS solutions tailored to your unique business environment. From initial assessment and strategic placement to seamless integration with your existing security stack, we ensure your system provides clear, actionable intelligence.
Contact Us today to get started.




